I came across a neat trick when looking into taking registry backups and would like to share what I found. This trick will work on Windows 7 and later operating systems.
First a little background. Let's take a look at the folder that the registry resides in and the core registry files (DEFAULT, SAM, SECURITY, SOFTWARE, SYSTEM):
%systemroot%\system32\config
There is one folder in particular that we are interested in:
%systemroot%\system32\config\RegBack
We can see that the RegBack folder is a copy of each of the registry hives. This is really cool because it allows us have at least one good copy of the registry that we can use to restore in case Windows gets to a state where it is unable to boot.
The question now is, how does this get backed up? There is a hidden scheduled task:
"\Microsoft\Windows\Registry\RegIdleBackup"
This is the task responsible for taking the snapshot that is saved in the RegBack folder. The problem is, this task in only scheduled to run once every 10 days. Some people might want to run it more often, or be able to run it on demand. Here is how to do it:
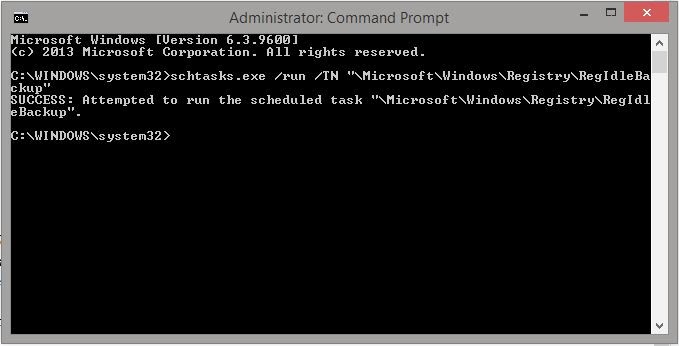
Open CMD as administrator
Type the following command:
schtasks.exe /run /TN "\Microsoft\Windows\Registry\RegIdleBackup"
Now you have a current snapshot of the registry! This can be restored manually from any PE environment that allows access to the file system.
r0cket's malware blog
Malware removal made easy.
Monday, December 16, 2013
Wednesday, November 14, 2012
FBI Online Agent
Another day, another screenlocker. These things are getting on my nerves...
This is a fairly straight-forward removal process.
- Reboot the PC into Safe Mode with Networking by repeatedly pressing the 'f8' key at the top of the keyboard until you get to the "Advanced Boot Options" menu
- Hold down Windows Key + R to get the run box open
- Clear out the text inside the run box and type "regedit.exe" (without the quotes), click "Ok"
- Navigate to the following key: HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- Look for an exe running from the following folder:
%userprofile%\Local Settings\Application Data\Microsoft\Windows\912\WSManHTTPConfig.exe
Keep in mind, the above exe name (WSManHTTPConfig.exe) and the folder that it is stored in (912 in my case) changes with each installation. I have underlined the part that changes with each installation.
All we need to do now is navigate to the folder and remove the exe itself. Here is how to do that:
- Open up the run box again the same way we did above.
- Type "control folders" (without the quotes) and click "Ok"
- Navigate to the "View" tab
- Tick "Show hidden files, folders, drives"
- UnTick "Hide Protected Operating System Files"
- Open the run box again
- Type "%userprofile%" (without the quotes) and click "Ok"
- Navigate to "Local Settings\Application Data\Microsoft\Windows\"
- Find the folder that was marked in the registry key that you found above (912 in my case)
- Delete that folder entirely (be careful not to delete any others, open the folder to be sure it is correct)
- Repeat steps 1-5 but tick the opposites (Hide files again)
- Run a malware scanner on the PC to ensure that you are rid of any leftovers
Subscribe to:
Posts (Atom)