Thanks to
Xylitol, here are a few registration keys that you can try to help get remote connection and removal before following the steps below:
3425-814615-3990
9443-077673-5028
I have seen a few of these rogues that have not been accepting the registration keys lately. Today I would like to go over with you the method that I use to connect remotely when the registration key does not work properly.
The first thing that we need to do is get the task manager open. To do this, you will need to use the key combination:
ctrl + shift + esc – this will bypass the rogue’s process killing mechanism.
Hold down Ctrl and click “New Task” – This will open a command prompt window for you. Launch regedit.exe from the command prompt window.
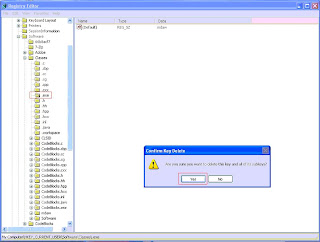
Remove the exe file association that is created by the rogue. This can be found at
HKEY_CURRENT_USER\Software\Classes\.exe - This file association is created by the rogue for the rogue’s use only so just delete the key.
After the file association has been removed, the rogue can no longer launch when trying to launch normal applications, so it is ok to kill the process now. I like to have the customer kill the process from the “Applications” tab as shown below.
At this point you can get your remote session up. Note that the file association has also been corrupted when launching the default browser from the start menu, so keep that in mind. From here, I recommend checking for any rootkit infections by using
TDSSKiller.
If any infections are found in TDSSKiller, please follow the instructions and reboot when asked. I will go over removal methods of the rootkits commonly associated with this infection in other posts.
Last step is to use your favorite malware scanner to ensure all traces have been removed.
MalwareBytes' Anti-Malware is my favorite. Make sure that you run a full scan to ensure that you have removed items from all user accounts and system restore.
Some of these have a worm infection called
Parite. You will find the infection in the log file of the MalwareBytes' scan that you just ran if it is present. This can be removed by using the
BitDefender Parite Removal Tool.
Finally, do yourself a favor and create a restore point ;)
Advanced Information
Registry Keys Modified
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Files Modified
%CommonAppData%\<random characters>
%LocalAppData%\<random characters>
%LocalAppData%\<random 3 chars>.exe
%Temp%\<random characters>
%UserProfile%\Templates\<random characters>







No comments:
Post a Comment